Ransomware: Should Organizations Pay or Not?
- Category: Blog
- Client: ASU Cybersecurity Bootcamp
- Project date: September 2023
To Pay or Not to Pay...
Ransomware threatens economies and continues to intimidate and potentially extort numerous institutions throughout the globe -- city governments, schools, hospitals, financial institutions, and businesses. Yet the question seems to always linger: if an organization is attacked by malicious actors with ransomware, should the organization pay or not?
Most folks would likely give a resounding “NO!” So why does the question persist?
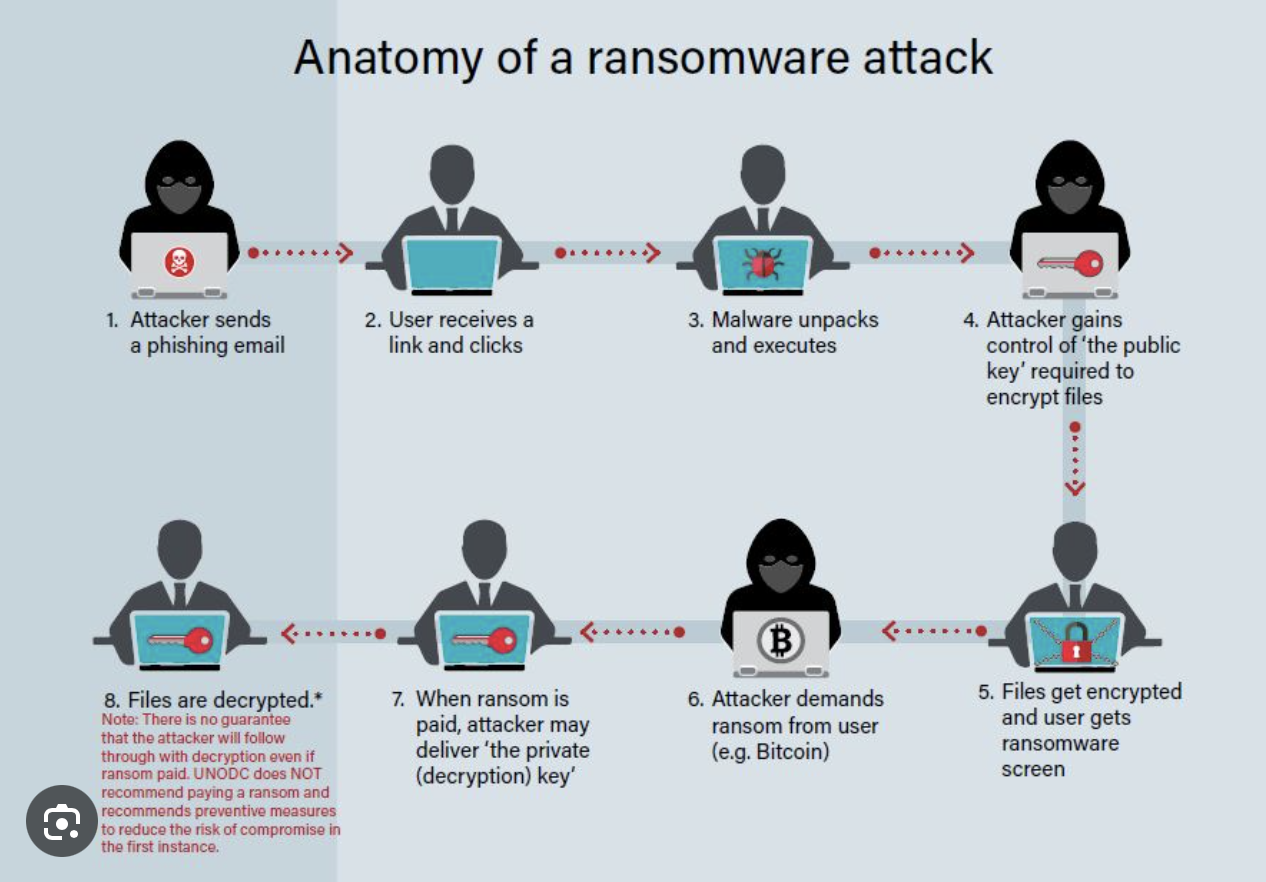
Some organizations simply pay the ransom because they do not have a choice. There are a lot of factors that need to be considered when making the decision to pay or not. For example, a business may cease to exist or patient’s lives may be at stake if an organization or hospital does not pay. Whether the cybersecurity program is lacking in an area, or some other reason - the attack happens and an organization pays. Regardless, the organization should report the ransomware attack to the appropriate local, state, and/or federal authorities [ex. FBI Internet Crime Complaint Center (IC3)].
Following the act of paying, the organization believes if they pay the ransom, the threat actors are going to uphold their end of the deal and not leak sensitive data, etc. Per cybersecurity company Cybereason - Indeed, and ZDNet produced a report in which researchers found ransomware gangs did not always honor their word after receiving a ransomware payment. Furthermore, researchers found that 80% of organizations that paid a ransom demand ended up incurring another attack. So if an organization pays the ransom demand, they are letting the threat actors know they are vulnerable and emboldening the threat actors for future attacks.
Third, another issue with paying a cyber ransom demand is assuming cyber insurance will cover the entire amount. As adults, we have all likely engaged with insurance companies, and likely feel some cautiousness when engaging with said insurance companies. While cyber insurance companies have negotiators for ransom demands, cyber incidents spiked in 2020, leading to an increase in payouts. As a result, premiums have increased, and not all ransoms may be paid in full. Additionally, cyber insurance companies will make renewal difficult by applying increased scrutiny on their clients’ security practices (ransomware.org).
In short, not paying ransomware demands is in the best interests of everyone, except the ransomware gangs of course. Law enforcement agencies recommend not paying because doing so encourages continued criminal activity by the threat actors. Furthermore, paying a ransom could even be illegal as it provides funding for criminal activity. Per Cybereason, the U.S. Treasury Department’s Office of Foreign Assets Control (OFAC) made this point clear in an advisory published in October 2020 (link below). Cybereason explains OFAC included malicious cyber actors, including ransomware attackers, in its cyber-related sanctions program. This means OFAC could impose penalties on U.S. persons who provide material assistance or sanctions violations (or pay a ransomware demand) - even if they did not know they were engaging in a transaction with a person that was prohibited due to sanctions (Cybereason). Moreover, the U.S. Department of Treasury also explains in its advisory the U.S. government is continuing to strongly discourage the payment of cyber ransom or extortion demands and emphasize the importance of cyber security practices to mitigate and prevent such attacks.
So what is the solution?
Preventing a ransomware infection in the first place through cybersecurity practices; however, always having a solid incident response plan to mitigate attacks and risk - even ransomware infections.